
A brand-new variation of the ViperSoftX information-stealing malware has actually been found with a wider variety of targets, consisting of targeting the KeePass and 1Password password supervisors.
The report originates from scientists at Pattern Micro, who specify that ViperSoftX now targets more cryptocurrency wallets than in the past, can contaminate various internet browsers besides Chrome, and is likewise beginning to target password supervisors.
Lastly, the most recent variation of the information-stealing malware functions more powerful code file encryption and includes to avert detection by security software application.
Worldwide targeting
ViperSoftX is an information-stealing malware that takes numerous information from contaminated computer systems. The malware is likewise understood to set up a harmful extension called VenomSoftX on the Chrome internet browser.
In the current variation evaluated by Pattern Micro, the targeted internet browsers now consist of Brave, Edge, Opera, and Firefox too.
The malware was very first recorded in 2020 as a JavaScript-based RAT (remote gain access to trojan) and cryptocurrency hijacker. Nevertheless, in November 2022, Avast reported that ViperSoftX was distributing a brand-new, far more powerful variation.
Avast stated at the time that it had actually found and stopped 93,000 attacks versus its customers in between January and November 2022, with the majority of victims living in the U.S., Italy, Brazil, and India.
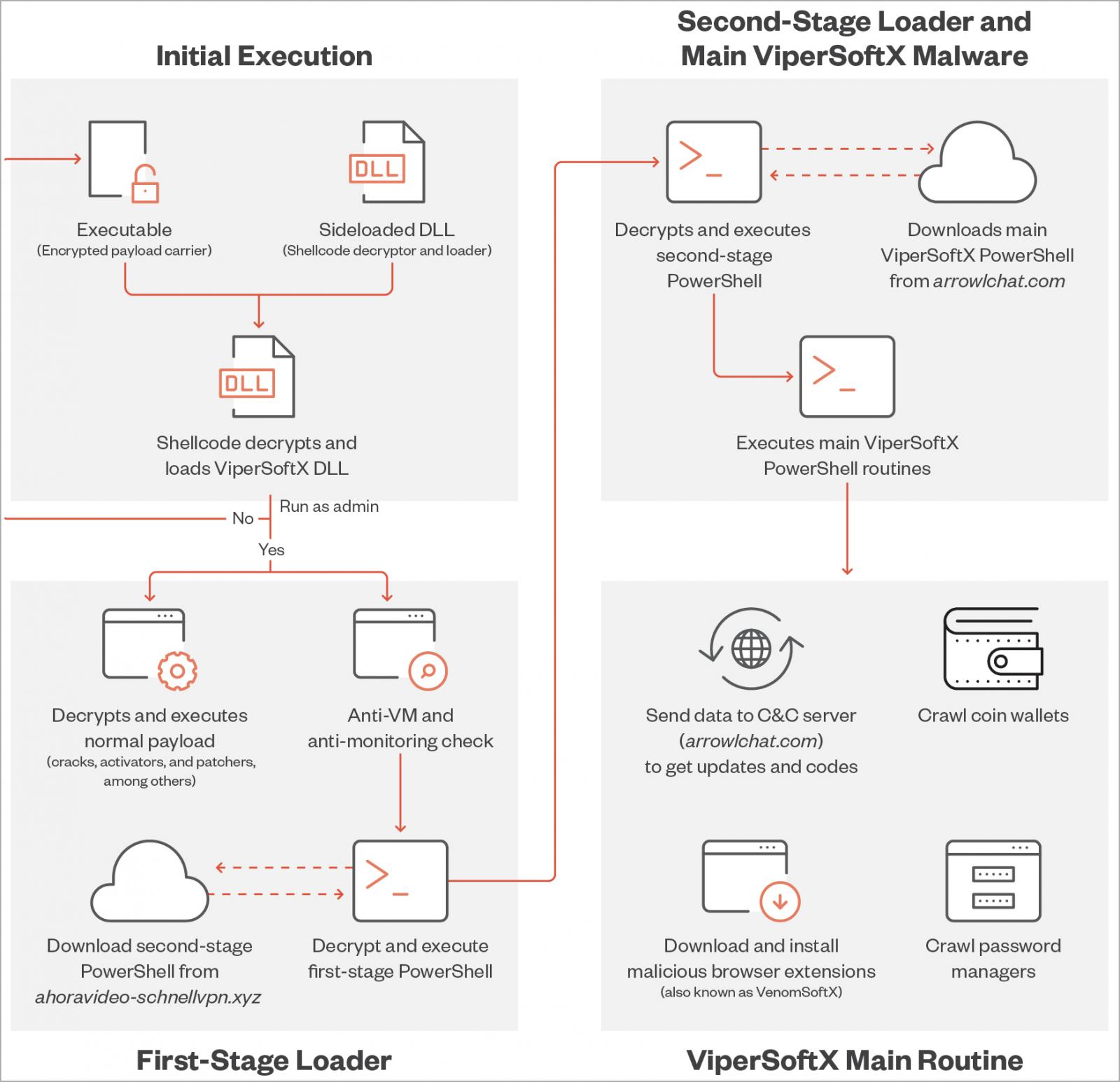
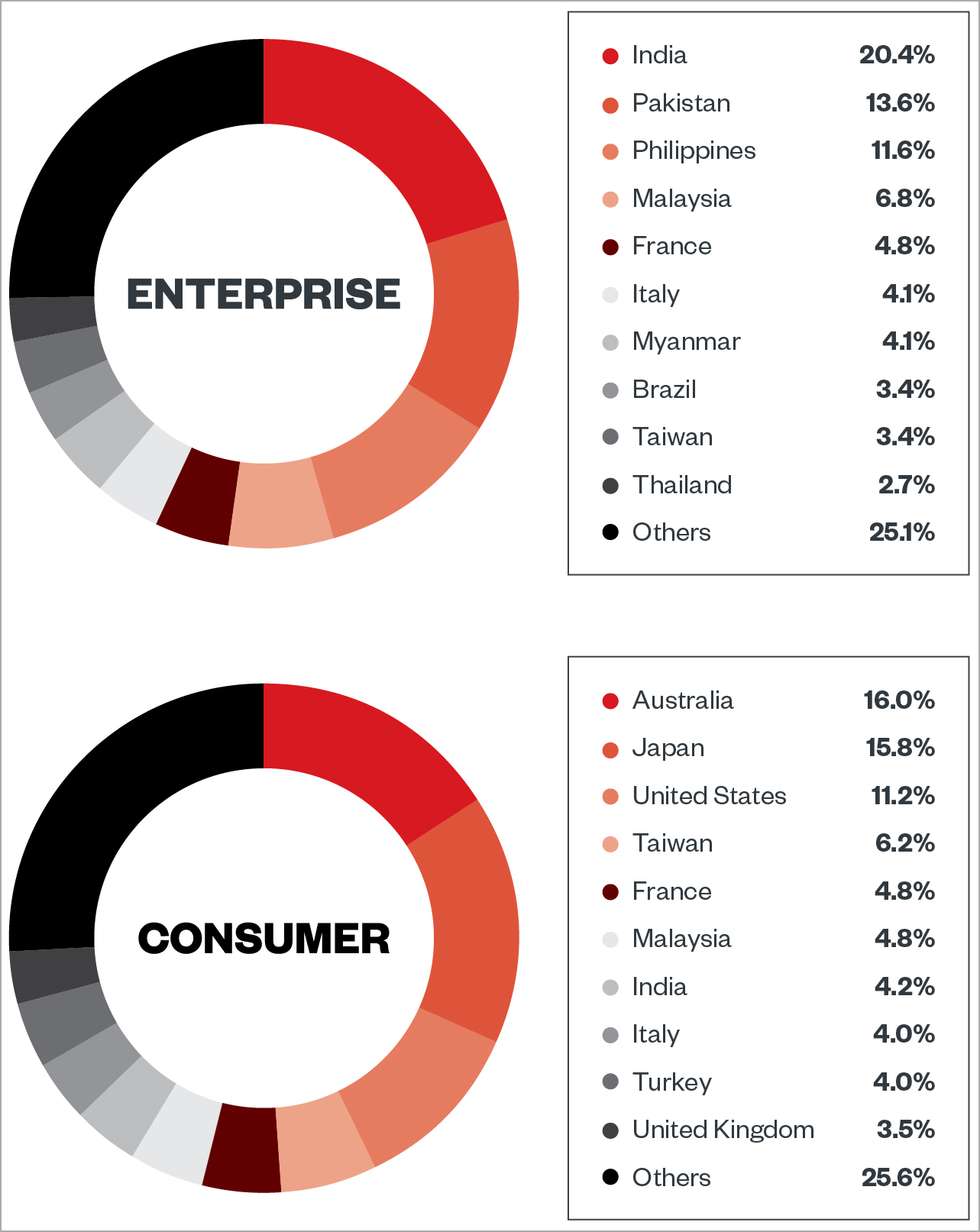
Today, Pattern Micro reported that ViperSoftX targets both the customer and business sectors, with Australia, Japan, the United States, India, Taiwan, Malaysia, France, and Italy accounting for over 50% of the found activity.
Based upon the experts’ observations, the malware generally gets here as software application fractures, activators, or crucial generators, concealing within benign-appearing software application.
Expanded targets
In the variation recorded by Avast, VenomSoftX targeted Blockchain, Binance, Kraken, eToro, Coinbase, Gate.io, and Kucoin crypto wallets.
Nevertheless, in the current version, Pattern Micro identified increased performance that takes from the following extra wallets:
- Armory
- Atomic Wallet
- Binance
- Bitcoin
- Blockstream Green
- Coinomi
- Delta
- Electrum
- Exodus
- Guarda
- Jaxx Liberty
- Journal Live
- Trezor Bridge
- Coin98
- Coinbase
- MetaMask
- Enkrypt
Of specific interest, Pattern Micro likewise reports that ViperSoftX is now looking for files related to 2 password supervisors, particularly 1Password and KeePass 2, trying to take information kept in their internet browser extensions.
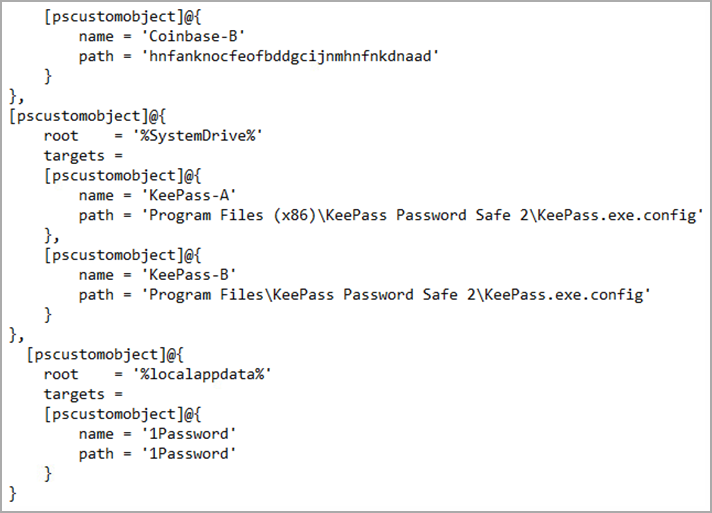
The experts examined if the malware included a make use of for CVE-2023-24055, which enables the retrieval of kept passwords in plaintext type however might not discover any proof of this exploitation.
Nevertheless, Pattern Micro informed BleepingComputer that it’s possible that if password supervisors are found, the hazard stars might target them with destructive activity in the later phases of the attack.
” Since the time of the writing, There was no clear information that we can collect from the codes of the malware other than to send out the information collected from getting the setup files. The KeePass area of the code was not present on external scientists’ reports, so we understand that it is a later addition,” Pattern Micro informed BleepingComputer.
” It is just obvious though that after collecting these intel (wallets and password setup) is that it will send it to its C2 ought to they exist.”
” One angle that we are checking out however is the possibility of getting back another set of codes/commands which would function as remote functions in order to continue with more functions (considering that it has the ability to work similar to a backdoor).”
Much better security
The brand-new variation of ViperSoftX utilizes numerous anti-detection, anti-analysis, and stealth-boosting functions, beginning with now utilizing DLL sideloading to carry out on the target system in the context of a relied on procedure, preventing raising any alarms.
Upon arrival, the malware likewise look for particular virtualization and tracking tools like VMWare or Process Screen and anti-virus items like Windows Protector and ESET prior to it continues with the infection regimen.
What’s most intriguing is the malware’s usage of “byte mapping” to secure its code, remapping the plan of shellcode bytes to make decryption and analysis without having the right map a lot more complex and lengthy.
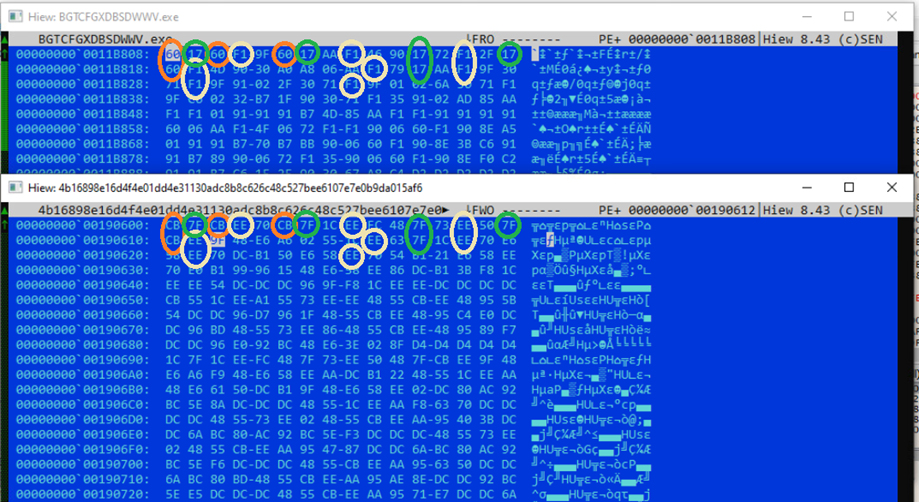
” We have actually likewise discovered that each sideloader DLL has its own set of executable and byte map, and a decryption effort returns an improperly reorganized shellcode if utilized with another ViperSoftX-related executable,” describes Pattern Micro in the reported
” This makes sure that the shellcode will not be decrypted without the right DLL considering that the latter includes the right byte map.”
Lastly, ViperSoftX includes a brand-new interaction blocker on web internet browsers, making C2 facilities analysis and destructive traffic detection harder.